Microsoft Security
Microsoft Defender for Endpoint: Architecture, Features, and Plans
What is Microsoft Defender for Endpoint (formerly Microsoft Defender Advanced Threat Protection)?
Microsoft Defender for Endpoint is an enterprise-grade Microsoft security platform for preventing, detecting, investigating, and responding to advanced threats on enterprise networks. It is built into Windows 10 and various Microsoft Azure services.
Here are key features of Defender for Endpoint:
Endpoint behavioral sensors—built into Windows 10, these sensors gather and process behavioral signals from the operating system. This data is sent to a cloud-based, private instance of Microsoft Defender for Endpoint.
Cloud security analytics—the solution gathers information from Microsoft optics across the ecosystem, including online assets and enterprise cloud products like Office 365. It employs big-data and device learning to translate these behavioral signals into detections, insights, and recommended responses to threats.
Threat intelligence—third-party partners and Microsoft hunters and security teams contribute threat intelligence to Defender for Endpoint. The solution uses the information to identify specific attacker techniques, procedures, and tools. It creates alerts when observing these indicators of attack in collected sensor data.
Microsoft Defender for Endpoint Architecture
Key Components
Microsoft Defender for Endpoint includes the following key components:
Admin portal—allows you to monitor endpoints, identify security incidents and respond to them.
Attack Surface Reduction (ASR)—analyzes attack surfaces and enforces rules that can reduce the attack surface on endpoints.
Endpoint Detection and Response (EDR)—helps you detect attacks happening in real time and respond to them directly on endpoint devices.
Behavioral blocking and containment—helps identify threats based on process behaviors on endpoints, even when attacks are already in progress.
Automated investigation and response—uses multiple inspection and analysis methods to prioritize alerts and execute automated responses.
Advanced threat hunting—lets you use a query-based tool to explore the past month of data, proactively looking for threat indicators and threat actors in the environment.
Threat analytics—reports from Microsoft security experts covering recent high-impact threats.
Onboarding and Setup
The following diagram illustrates how you start using Microsoft Defender for Endpoint in your organization.
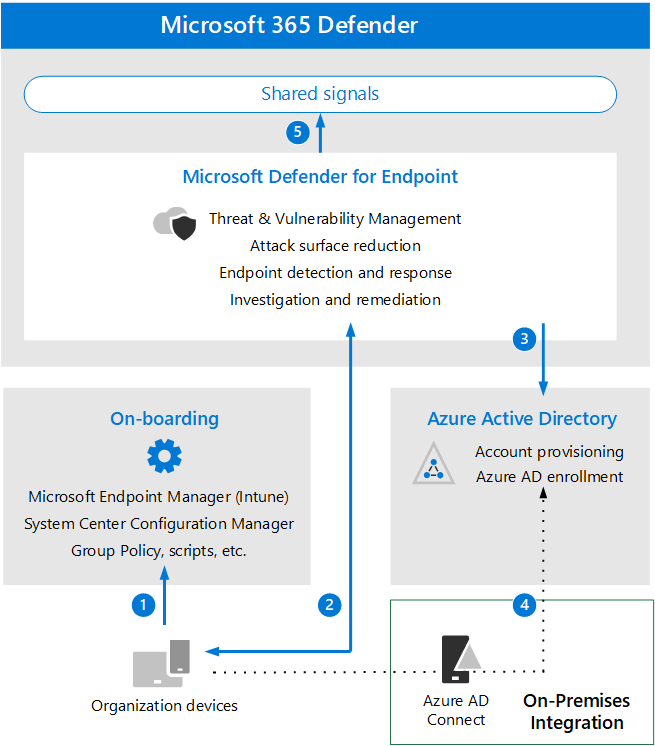
The diagram shows the process for onboarding endpoint devices so they can be protected by Defender for Endpoint:
Onboard devices through Microsoft Intune, System Center Configuration Manager, scripts, or other supported management tools.
Devices start sending signals to Microsoft Defender for Endpoint.
Managed devices join or enroll in Azure Active Directory (Azure AD).
Windows devices deployed on-premises, and enrolled in Windows Active Directory, are synchronized using Azure AD Connect.
Once the process is complete you can view Microsoft Defender for Endpoint alerts, responses, and other data in Microsoft 365 Defender.
Related content: Read our guide to Microsoft 365 Defender
Microsoft Defender for Endpoint Features
Please note that Microsoft Defender for Endpoint has been split into two editions—Plan 1 and Plan 2. Plan 2 contains all the features below, while Plan 1 has only some of them. Learn more below.
Threat and Vulnerability Management
This feature helps you identify vulnerabilities and misconfigurations in endpoint devices in real time, without needing to deploy special agents or perform vulnerability scans.
How it works
Threat and vulnerability management uses sensors on endpoints to detect vulnerabilities. It can prioritize vulnerabilities based on an analysis of all detections in your organization, whether endpoints contain sensitive data or not, and the threat landscape.
This capability is fully cloud-based, integrates with the rest of the endpoint security stack (Defender for Office 365, Defender for Identity, and Defender for Cloud Apps). It leverages the Microsoft Intelligent Security Graph and application analytics knowledge base, which contains trillions of security data points from Microsoft software deployed worldwide.
Benefits
Threat and vulnerability management can help reduce your organization’s risk as a result of security vulnerabilities. By ensuring endpoints are hardened, you improve resilience to cyber attacks.
Attack Surface Reduction (ASR)
ASR can help you automatically reduce attack surfaces on endpoint devices by blocking certain capabilities at the operating system level and controlling applications and web access.
How it works
ASR is based on rules, which can control software behaviors like launching executables and scripts, including scripts that are obfuscated or otherwise suspicious, and software performing actions that are not typical for normal work activity.
Because these rules can have an impact on users and might block legitimate software functionality, it is possible to run ASR in audit mode, to identify what specific rules would block, and also in a special “warn mode,” which warns users that the content they are trying to view is blocked, but allows them to unblock it for 24 hours.
Benefits
ASR rules can help remove opportunities for attackers to compromise endpoint devices or networks. By applying as many rules as possible, you reduce your attack surface and eliminate many possible attacks against your endpoints.
Next-generation Protection
This feature includes the basic protection offered by Microsoft Defender Antivirus, and additional protection against advanced threats.
How it works
Next-generation protection includes the following advanced capabilities, in addition to legacy antivirus:
Behavioral and heuristic antivirus protection—always-on scanning and monitoring of file and process behavior, identifying suspicious activity using predetermined heuristics, or by comparison applications to a normal behavioral baseline. This capability can block applications that appear to be unsafe, even if they are not detected as malware.
Cloud-delivered protection—fast updates of threat intelligence data to ensure endpoints are protected against the latest threats.
Protection and product updates—pushes updates of Microsoft Defender Antivirus to endpoints, even if it is working in passive mode. Supports distribution of updates through Windows Server Update Service (WSUS), Microsoft Endpoint Configuration Manager, or the regular methods you use to deploy Microsoft updates to endpoints.
Benefits
Next-generation protection is able to detect and block advanced and unknown threats, protecting against malware and exploits that cannot be detected by legacy antivirus.
Endpoint Detection and Response (EDR)
This feature enables security teams to detect attacks in real time, as they occur, and respond to them via direct access to the endpoint.
How it works
EDR alerts security analysts about suspicious events on endpoints, allows them to prioritize alerts and quickly investigate the full scope of the incident, and take immediate action to mitigate threats.
The process starts from an alert created in the EDR system. EDR aggregates alerts using the same attack techniques, or associated with the same attacker, making it easy for analysts to respond to threats occurring across multiple endpoints. It collects behavioral data such as process activity, network activity, kernel and memory usage, login activities, registry changes, and file changes. All data is stored for six months, enabling deep investigation of attacks to see their origins.
Benefits
EDR lets you adopt an “assume breach” mentality, being ready for breaches on endpoint devices, rapidly investigating them, and taking action to contain and eradicate threats before they can do damage.
Automated Investigation and Remediation (AIR)
This feature lets you reduce alert volumes, helping security teams focusing on the most important alerts and identifying real security incidents.
How it works
AIR uses multiple inspection algorithms which reduce alert volume, and suggest automated remediation actions for high priority alerts. These remediation actions appear in the Action Center, allowing analysts to view pending actions, approve or reject them, and also undo actions if necessary.
Benefits
AIR reduces alert fatigue and helps your organization’s security analysts respond to more critical endpoint incidents in less time.
Microsoft Secure Score for Devices
This feature provides an automated assessment of an entire enterprise network, helping you identify systems that are unprotected and take action to improve security.
How it works
Secure Score for Devices identifies unprotected systems and automatically performs actions to improve their security posture. The results of security assessments can be viewed in the Microsoft 365 Defender portal. Secure Score for Devices shows a single score for the entire network, indicating how many endpoint devices are secure against cyber attacks.
This feature is able to scan and detect the security posture of applications, operating systems, networks, user accounts, and specific security controls.
Benefits
Secure Score for Devices provides a holistic view of endpoint security across an enterprise network, allowing you to perform rapid assessments, plan and prioritize security remediation efforts.
Microsoft Threat Experts
This is Microsoft’s threat hunting service, provided by human security experts. Microsoft experts provide expert-level monitoring and proactive hunting of threats in your environment. The feature provides targeted attack notifications for threats discovered by Microsoft experts.
Benefits
Microsoft Threat Experts complements your in-house security team with Microsoft expertise, who use advanced techniques to identify sophisticated and evasive threats in your environment, which otherwise could have been missed.
What Are Plan 1 and Plan 2?
Microsoft Defender for Endpoint was originally released as a complete endpoint detection and response (EDR) and advanced threat protection solution. In November 2021, Microsoft released a limited edition of the product, which provides device security for Windows, MacOS, Android, and iOS devices at a lower price for organizations with more limited budgets and security requirements.
The original and new versions of the Microsoft Defender for Endpoint were renamed as follows:
Defender for Endpoint Plan 1—this is the new name for the limited edition of the product intended for smaller businesses
Defender for Endpoint Plan 2—this is the new name for the full version of the product, which was previously named simply “Microsoft Defender for Endpoint”
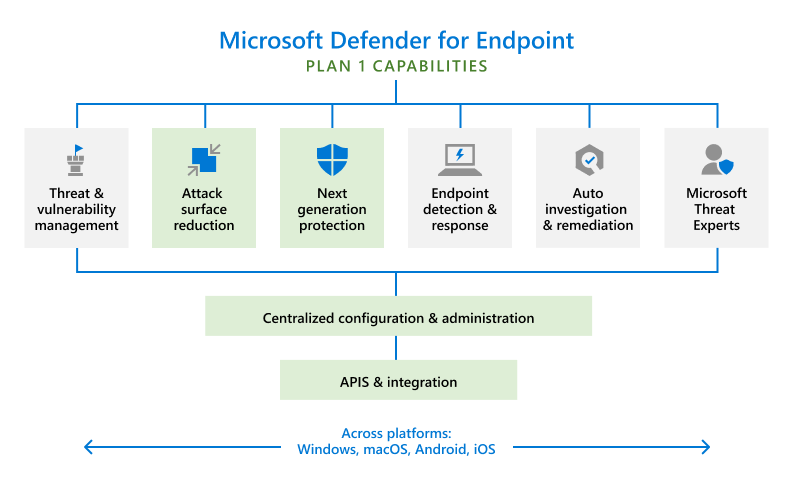
The following diagram can help you understand the differences between Plan 1 and Plan 2. The green boxes below are the features only available in Plan 1. Plan 2 includes all the features, including the ones colored in gray.
Best Practices for Addressing False Positives and Negatives in Defender for Endpoint
False positives are a common problem in endpoint protection. A false positive is an alert that indicates malicious activity, although in reality it is not a threat. The opposite problem is a false negative - a real threat that was not detected by the solution. Microsoft 365 Defender provides several capabilities that can help you deal with and minimize false positives and negatives.
Review and Classify Alerts
Defender for endpoint provides two simple tools that can help address false positives:
Suppressing alerts - if you see an alert that does not represent a threat, or may be a true positive but is unimportant, you can suppress it to stop getting alerts for that entity.
Classifying alerts - in addition to suppressing alerts, you should also classify the alert as “true positive”, “benign true positive”, and “false negative” to help the Defender of Endpoint engine learn to identify similar false positives.
Review Remediation Actions
Defender for Endpoint performs remediation actions automatically when it detects security issues on endpoints. Some actions are triggered manually by your security team via Live Response, which provides direct access to the endpoint to mitigate threats.
When reviewing alerts, remember to look at remediation actions as well. If the alert is false negative and remediation actions were taken, you can usually undo them. For example, you can restore quarantined files. Keep in mind that Live Response actions cannot be undone.
Review or Define Exclusions
Microsoft Defender for Endpoint lets you define exclusions, which specify that in certain cases a remediation action should not be performed. After discovering false positives and unwanted remediations, you can define exceptions to prefer the solution from performing these actions again. For example, you can define specific files that won’t be quarantined.
The exclusion process involves two elements:
Exclusions for Microsoft Defender Antivirus - these exclusions should be defined sparingly and should only include files, folders, and processes that are resulting in false positive.
Indicators for Microsoft Defender for Endpoint - these are indicators of compromise (IoC) that trigger alerts and remediations. You can specify files, IP addresses, or URLs that should be omitted from scans. Add “allow” indicators to exclude entities from next-generation protection.
Submit Files for Analysis
If you are not sure if a file is truly malicious or not, you can submit it to Microsoft for investigation. You can track your submissions and receive a response for each submission. When you submit a file, it is automatically scanned and the system provides immediate information - for example, if the file was previously submitted, you see the previous resolution. If not, you will receive a response from a human analyst at Microsoft.
Review and Adjust Your Threat Protection Settings
You can fine tune your threat protection options to reduce the number of false positives. Consider adjusting the following options to meet your organization’s requirements:
Cloud-delivered protection - by default this is not enabled. If you set it to High, High+, or Zero Tolerance, you will be alerted about more issues but will also experience more false positives.
Remediation for potentially unwanted applications (PUA) - PUA is software that is not malware, but can cause unwanted effects on endpoints such as slowdown, ads, or installation of other programs. Consider running PUA protection in audit mode initially, or test it on a small group of endpoints, to identify false positives.
Automated investigation and remediation (AIR) - this feature examines alerts and provides a verdict for each piece of evidence - Malicious, Suspicious, or No Threats. Depending on your settings, it can also perform automated remediation. Tune AIR settings to the level of sensitivity and automation your organization needs.
Managed Detection & Response
Microsoft Security with BlueVoyant
Deploy the Microsoft security tools you already have and eliminate the headaches and cost of disparate security products.

Additional Readings

Microsoft Security
Microsoft 365 Defender

Microsoft Security
Microsoft Defender for Office 365: Workflow, Features, and Plans

Microsoft Security
What Is Microsoft 365 E5 and Top 10 Security Features

Microsoft Security
Microsoft Security: Architecture, Tools, and Technologies

Microsoft Security
What Is Azure Sentinel (Renamed to Microsoft Sentinel)?

Microsoft Security
Microsoft Sentinel Deployment Best Practices - 2nd Edition

Microsoft Security
Microsoft Sentinel Updated One-Page Diagram
